The log file navigator, lnav, is an enhanced log file viewer that takes advantage of any semantic information that can be gleaned from the files being viewed, such as timestamps and log levels. Using this extra semantic information, lnav can...
As an industry, we aspire to something that delivers on our collective vision of fully-automated, self-governing infrastructure. In the 00s we called it autonomic computing, then software defined data center (SDDC) and, now, IaC. Sadly, IaC...
Configuring Jenkins To Build WebGoat We’re going to scan a known vulnerable webapp, WebGoat, which is an OWASP project used for learning basic web penetration testing skills and vulnerabilities. A good scanner should find a lot of...
Companies selling “security scorecards” are on the rise, and have started to become a factor in enterprise sales. We have heard from customers who were concerned about purchasing from suppliers who had been given poor ratings, and...
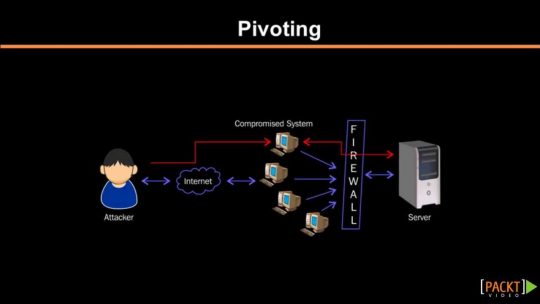
I don’t often come get a chance to use pivot techniques, so I sometimes find myself searching for reminders about various methods and their trade offs. I put together this list of common pivot techniques I have used, along with a quick...
Fail2Ban is an intrusion prevention framework written in Python that protects Linux systems and servers from brute-force attacks. We can setup Fail2Ban to provide brute-force protection for SSH on our server, this will ensure that the server...